How to integrate SonarQube and Jenkins

Simple and efficient way to do assess the code quality is to integrate SonarQube with your CI.
SonarQube is available both in Opensource and Enterprise. You can configure it on-prem as well as use the SaaS version of SonarQube for your CI/CD workflows.
Here, we look at integrating SonarQube with CI tool Jenkins. There are official documentation available , here we see real time integration with screenshots and all necessary configurations required for the same.
Pre-requisites :
Install Jenkins and SonarQube , if not please follow this script to get Jenkins and SonarQube installed.
Process
Once the tools are in place,
let us assume , Jenkins is at http://localhost:8080 and SonarQube at http://localhost:9000.
SonarQube configurations
Create a token in SonarQube by logging into SonarQube. Select the Profile and choose MyAccount

Generate token

Keep the token in a safe location, which would be used in a later stage.
Jenkins Configurations
- Configure SonarQube Scanner
Log into Jenkins , Go to Manage Jenkins > Tools Section .

Add the SonarQube Scanner installation details .
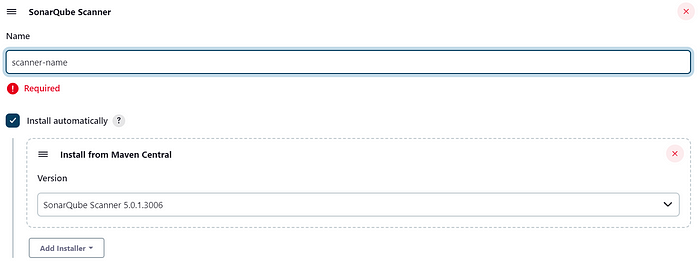
This name would be used in the Jenkins pipeline.
2. Create a credential to connect Jenkins and SonarQube server.
For that, create a credential of kind Secret Text and add the token generated from the SonarQube in the initial step.

3. Invoke the SonarQube server connections
Go to Manage Jenkins > System configurations
Select the check-box of Injecting Environment variables and add the details of the SonarQube Server


The authentication token must be the credential that is created in Step 2.
Keep a note of the name used in this configuration.
4. Jenkins file:
stage('SonarQube Code Analysis') {
steps {
dir("${WORKSPACE}"){
// Run SonarQube analysis for Python
script {
def scannerHome = tool name: 'scanner-name', type: 'hudson.plugins.sonar.SonarRunnerInstallation'
withSonarQubeEnv('sonar') {
sh "echo $pwd"
sh "${scannerHome}/bin/sonar-scanner"
}
}
}
}
}
stage("SonarQube Quality Gate Check") {
steps {
script {
def qualityGate = waitForQualityGate()
if (qualityGate.status != 'OK') {
echo "${qualityGate.status}"
error "Quality Gate failed: ${qualityGateStatus}"
}
else {
echo "${qualityGate.status}"
echo "SonarQube Quality Gates Passed"
}
}
}
}Note: You can add Sonar Project properties in the stage, as well as a separate file in the root directory where the application code resides, in the above case, the sonar-project.properties file was created along with the application code.
# sample file
sonar.projectKey=sample-app
sonar.projectName=sample-app
sonar.projectVersion=1.0-SNAPSHOT
sonar.language=py
sonar.python.version=3.8 # Specify the Python version you are using (e.g., 2.7 or 3.x)(Optional) If you want to add the sonar properties in the Jenkins file itself, then the Jenkinsfile would look like this.
stage('SonarQube Code Analysis') {
steps {
dir("${WORKSPACE}"){
// Run SonarQube analysis for Python
script {
def scannerHome = tool name: 'scanner-name', type: 'hudson.plugins.sonar.SonarRunnerInstallation'
withSonarQubeEnv('sonar') {
sh "${scannerHome}/bin/sonar-scanner \
-D sonar.projectVersion=1.0-SNAPSHOT \
-D sonar.qualityProfile=<qualityprofilename> \
-D sonar.projectBaseDir=/var/lib/jenkins/workspace/Snyk-Testing/snyk-code-container-scan/appcode \
-D sonar.projectKey=sample-app \
-D sonar.sourceEncoding=UTF-8 \
-D sonar.language=python \
-D sonar.host.url=http://<URL>:9000"
}
}
}
}
}With this Jenkins is integrated with SonarQube, once the code is built , it could be sent to SonarQube for code quality. The above stages would help to create a project in SonarQube against this pipeline execution and the results would be available in SonarQube > Projects section.
Quality Gates could help you to further refine the code quality and customize based on your requirement. Based on the quality gate selected for the SonarQube project, the results would be sent back to the Jenkins pipeline through the second stage.
Once the analysis is completed, the SonarQube Project analysis report looks like below.

Jenkins Console output would look like :
Code Analysis:

Code Quality:

To see the complete DevSecOps pipeline, visit this blog.